| |
 |
|
| |
|
|
|
| |
GIGABYTE's Ultra TPM Explained |
|
|
| |
|
| |
|
|
| |
In today's computing environment, security threats such as viruses, worms, trojan attacks, malicious hacking and data/identity theft, etc. are not only happening more frequently, but the cost to victims of such attacks are also on the rise. While software solutions are able to protect data to a certain degree, a higher level of security measures is needed to ensure you do not become the next victim.
That is where a hardware based solution such as TPM (Trusted Platform Module) technology can help. Trusted Platform Modules are hardware based security microcontrollers that store keys, passwords and digital certificates and protects this data from external software attacks and physical theft.
Recognizing the need to protect users against today's computing security threats, GIGABYTE is the first motherboard manufacturer to equip their motherboards with an onboard TPM Module from Infineon with 2048 bit encryption key. But, they didn't stop there. GIGABYTE has paired their TPM module with a security software interface called GIGABYTE Ultra TPM, providing the Industry's highest level of data security through a hardware + software design.
In order to better understand GIGABYTE Ultra TPM and how it works, let's first get a crash course in how data security works.
|
|
|
| |
|
|
| |
Encryption and Decryption Explained
Most data security solutions, whether they are software or hardware based, rely on a process of encryption and decryption to secure digital data. Encryption takes your data and transforms it, making it unreadable to anyone that doesn't have a "key" to read it. The key basically tells how that information was transformed, and acts as a password for the data. Once you have the key, you are able to undo the encryption, a process called decryption, making the data readable again.
Key size basically determines the level of security; 1 bit keys being the least secure, all the way up to the 2048 bit key found in GIGABYTE's Ultra TPM. How secure is 2048 bit security? The number of possible combinations from a 2048 bit number is 22048, which is 3.23 x 10616. That is 3 followed by 616 zeros or
30000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
00000000000
That is how many possible different number combinations a 2048 bit key has. A computer capable of one million instructions per second would have to work for 1014 years to crack the key. Is it any wonder why this is considered military strength security?
|
|
|
| |
|
|
| |
Software vs Hardware + Software Based Security
There are of course several different ways in which data can be encrypted. There are software only based solutions, hardware and software combination solutions and GIGABYTE's Ultra TPM. |
|
Software based Encryption |
TPM Hardware Based Security
|
GIGABYTE Ultra TPM
Hardware + Software based Encryption
|
|
- Platform authentication with integrated security solution
- Keys and secrets protected by dedicated hardware
|
- Platform authentication with integrated security solution
- Keys and secrets protected by dedicated hardware
- Key can be deleted completely from system offering the highest level of security possible
|
- Low protection against logical attacks
|
- High protection against logical attacks
|
- High protection against logical attacks
|
- No protection against physical attacks
|
- High protection against physical attacks
|
- Highest level of protection against physical attacks
|
|
|
|
|
| |
Software Only Based Security
There are many different software packages that can provide software-enabled data encryption such as Bitlocker or FileVault. Software based encryption programs use software algorithms to encrypt and decrypt data. But encryption is a mathematically intensive process, and software-based encryption demands substantial processing power from the CPU. This means you are unable to do other things when encrypting or decrypting data using a software application.
Software-based encryption packages may protect against casual attempts to hack protected data, but it has long been known that there are ways to break this type of data encryption with the right sort of tools. Long story short, software only based encryption is not as secure as hardware based and is much more CPU intensive.
TPM Hardware Based Security
TPM or Trusted Platform Modules have been on the market for a number of years now, most notably in secure notebooks, gaming consoles such as the XBOX, cable and satellite set top boxes, hard drives and a host of other devices that require some level of security. However, GIGABYTE is the first manufacturer to use TMP hardware security chips on a motherboard level. So, how do TPM's work?
A major flaw with software security applications is that the encrypting and decrypting of data is done by the CPU. As mentioned above, not only does this create a drain on CPU resources, but also creates a window of opportunity for unauthorized access to the data, as the data stored on the hard drive needs to be accessed by the CPU for processing.
|
|
| |
A TPM is different in that all of the encryption and decryption process is handled by the TMP microcontroller, so the data doesn't need to be accessed by the CPU at all, freeing up important CPU resources and eliminating the window of threat. In order to grant access to this data, a TPM module has an assigned a key, in the case of Infineon's TPM module a 2048 bit key, that is used to encrypt the data. If the user tries to view this encrypted information without the key, not only will they be unable to decrypt it, but they are also unable to see that that any data exists at all.
GIGABYTE uses a TPM microcontroller from Infineon. Before I talk about GIGABYTE Ultra TPM and how it works, let's first look at how users can use just the Infineon TPM implementation on its own. After enabling the TPM controller in BIOS, users need to install the Infineon TPM driver & utility (as I mentioned, this is a hardware plus software solution). After Initialization (users will be asked to create a password to gain access to the key), a TPM icon will appear in the taskbar. |
|
|
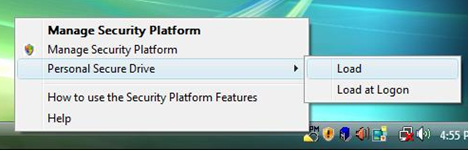
Users then right click the TPM icon and choose "load the Personal Secure Drive".
|
|
Then Infineon utility will ask for the 6 digit password previously set during initialization process.
|
|
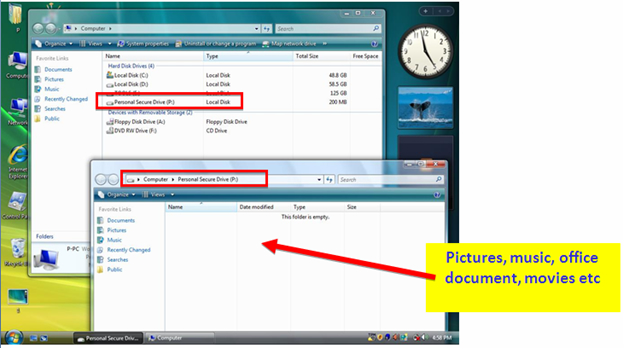
Then Personal Secure Drive will appear as a normal drive, any files (picture, office document, movies etc) you store in this drive will be automatically encrypted.
|
|
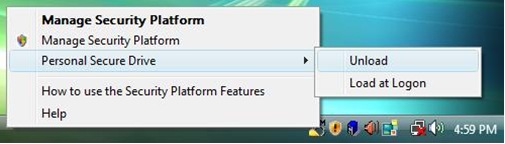
When users want to leave or finish accessing with the encrypted files in the Personal Secure Drive, they need to right click the icon, and choose "Unload".
|
|
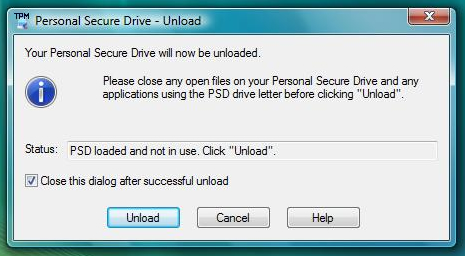
A re-confirm box will appear, users then press "Unload". |
|
|
| |
Downsides of Typical TPM Implementations
So, that is how Infineon's TPM module works along with their software interface. As you can see, there are a couple of drawbacks with this scenario.
- First of all, it is a bit complicated and there are many steps to follow.
-
The 2048 bit encryption key which protects the encrypted files in the Personal Secure Drive is stored in the HDD. If someone steals the hard drive from the system, they still have access to both the data and the key
-
There is a 6 digital password that protects access to the 2048 bit encryption key. But this password can be cracked. If someone knows or cracks the 6 digit password (normally it’s easy since most people use their name, birthday etc to make up the password), and can get access to the PC (during lunch for example), then the data is no longer secured because the 2048 bit encryption key is also in the PC!!!
-
Users also need to manually load / unload the Personal Secure Drive and enter the password every time. This makes it not very user friendly.
|
|
| |
GIGABYTE Ultra TPM |
|
 |
With Infineon's TPM chip built-in, GIGABYTE provides TPM hardware-based encryption and decryption with digital signature keys to ensure a maximum level of data protection with 2048 bit encryption. GIGABYTE Ultra TPM provides an added layer of security by allowing users to store their digital signature key on a USB thumb drive, so that when they step away from their system, they can take the key with them, locking up their data and preventing unauthorized access while they are away. When making the portable user key, GIGABYTE Ultra TPM auto deletes the user key in the hard drive, ensuring the maximum level of data protection.
|
|
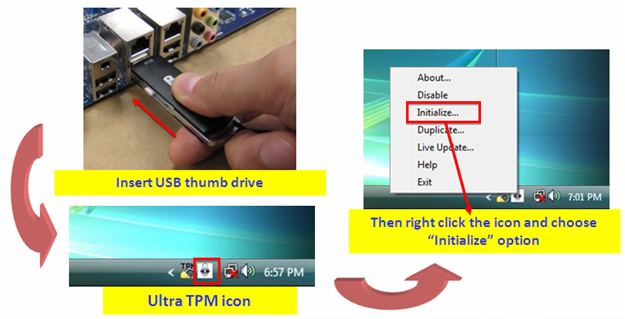
Here is how GIGABYTE Ultra TPM works. First, users need to install the GIGABYTE Ultra TPM utility from driver CD. Then Ultra TPM icon will appear in the taskbar.
|
|
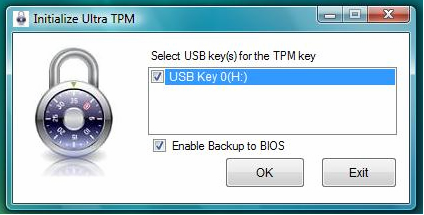
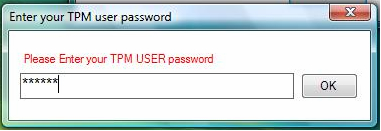
Then, the Ultra TPM utility will ask users to make a USB TPM key, also giving the users the choice to copy the TPM key in backup BIOS (in case the USB TPM key is lost or damaged). While keeping a key in the BIOS is less secure, it is still more secure than most typical TPM implementations which store a copy of the key on the hard drive. If that hard drive is stole, someone then has access to not only the data, but the key as well. Basically, if users are afraid of losing the key, they should considering keeping a copy in the BIOS. Of course, GIGABYTE Ultra TPM allows users to make as many keys as they want, but the more keys are made, obviously the greater chance someone has to get a hold of the key.
|
|
|
As the thumb drive key is being made, GIGABYTE Ultra TPM will automatically delete the 2048 bit encryption key stored in the HDD.
|
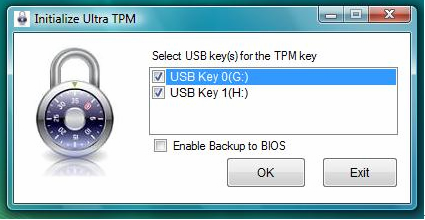
Users can also choose to make multiple keys at the beginning.
|
|
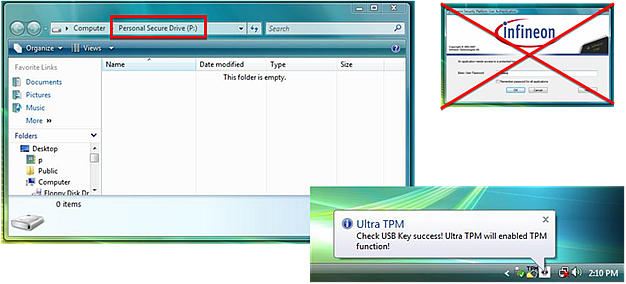
That is it. Setup is complete. When the USB TPM key is inserted, the Personal Secure Drive will automatically appear. Users no longer have to enter a password.
|
|
|
| |
The Benefits of GIGABYTE Ultra TPM
Obviously there are some key benefits to this type of implementation.
- Security, manageability and flexibility that surpasses software-based encryption.
- No password required. Users don't have to remember and keep entering their password. This also means there is no password for someone to crack.
- Quick and effortless protection of data; plug in USB key to access data, or remove to safeguard.
- Keeps data secure even when users are away from computer.
- Optional backup of key stored in BIOS in case of misplaced key.
- Very low CPU utilization. As all the encryption and decryption is done by the TPM, users are able to do other tasks simultaneously.
While no security system is 100% secure, GIGABYTE Ultra TPM provides the industry's highest level of military grade security, and at the same time, makes it easy enough for anyone to use. Whether protecting important data at the office or ensuring your kids don't accidentally delete things off the home computer, GIGABYTE Ultra TPM has you covered. Think of it as your own personal 24/7 security force. |
| |
|
|
|
|
| |
|
|
| |
All intellectual property rights, including without limitation to copyright and trademark of this work and its derivative works are the property of, or are licensed to, GIGA-BYTE TECHNOLOGY CO., LTD. Any unauthorized use is strictly prohibited. |
|
| |