ASPEED AST2400 & AST2500 Security Vunerabilities (CVE-2019-6260)
Update 4th September 2019 – GIGABYTE has discovered an issue when customers using an older Linux Distributition update their BMC firmware to the new version containing the CVE-2019-6260 patch - the installation will fail.
Affected OS: Debian 8 / Redhat 7.3 / CentOS 6.9
Root Cause: Host access ASTSoC P2A (CVE-2019-6260 item 3) for standard VGA 2D driver
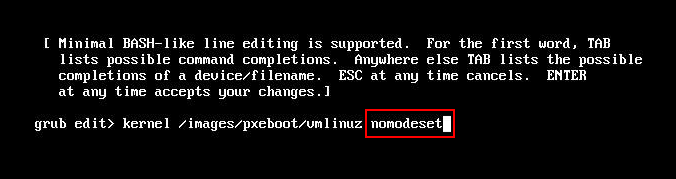
Solution: Add "nomodeset" in kernel boot option, please refer to the below images:
(RedHat 7.3)

(CentOS 6.9)
Update 19th August 2019 – GIGABYTE is aware of a recently security vulnerability, CVE-2019-6260, which affects GIGABYTE server motherboards and systems using ASPEED AST2400 or AST2500 SOC to implement BMC functionality. According to the National Vulnerability Database, the ASPEED AST2400 and AST2500 BMC hardware and firmware implement Advanced High-performance Bus bridges, which can allow arbitrary read and write access to the BMC's physical address space from the host.
If you are using a GIGABYTE server product that uses an ASPEED AST2400 or AST2500 SOC, it is recommended the following action be taken to mitigate this security vulnerability:
1. Download an updated version of the server product BIOS which contains CVE-2019-6260 security patch update.
The BIOS update with CVE-2019-6260 security patch is currently being updated for each server product according to the following schedule (please see each product page - support section to download the latest BIOS version)
| CPU / CHIPSET | BMC FIRMWARE | BMC SOC | BIOS UPDATE SCHEDULE |
|---|---|---|---|
| Intel Xeon E (Mehlow) | AMI | AST2500 | Available |
| AMD EPYC (Naples) | AMI | AST2500 | Available |
| Cavium ThunderX2 | AMI | AST2500 | Available |
| 2nd Gen. Intel Xeon Scalable (Cascade Lake) | AMI | AST2500 | Available |
| Intel Xeon D-2100 (Skylake D) | AMI | AST2500 | Available |
| AMD EPYC (Naples) | Vertiv | AST2400 | Available |
| Cavium ThunderX | Vertiv | AST2400 | Available |
| Intel Xeon E3-1200 v6/v5 (Greenlow) | Vertiv | AST2400 | Available |
| Intel Xeon D-1500 (Broadwell DE) | Vertiv | AST2400 | Available |
| Intel Xeon E5-2600 v4/v3 (Grantley) | Vertiv | AST2400 | Available |
2. Download an updated version of the server product BMC firmware which contains CVE-2019-6260 security patch update.
A. For server products using AMI BMC Firmware (with Megarac SP-X management interface):
- AMI BMC Firmware: Available (Version 2.83)
(please see each product page - support section to download the latest firmware version)
B. For server products using Vertiv BMC firmware (with Avocent Mergepoint 2.0 management inferface):
- Vertiv BMC Firmware for AST2400 (x86): Available (Version 8.83_4.83)
- Vertiv BMC Firmware for AST2400 (Arm): Available (Version 772_372)
- Vertiv BMC Firmware for AST2500: Available (Version 1.84)
(please see each product page - support section to download the latest firmware version)
For further information on CVE-2019-6260, please see the NATIONAL VULNERABILITY DATABASE CVE-2019-6260 detail page: https://nvd.nist.gov/vuln/detail/CVE-2019-6260
For any further assistance regarding this issue please contact your GIGABYTE sales representative, or file a new support ticket at https://esupport.gigabyte.com

















