Introduction
A seamless shield for your workspace is constructed by integrating access control with thermal sensors and facial recognition technology. Our solution allows organizations in various industries to act rapidly with real-time temperature screening and access control integrated into a single device. We believe that prevention is better than a cure. Facial recognition technology is 100% contactless and it can prevent the spread of viruses through touch. Regardless of whether they are company employees or visitors, access control and temperature measurement can simultaneously be performed easily and rapidly by our solution, enabling companies to reduce the time and manpower spent on this task.
Scenario
We can master identification, access control, and body temperature screening within one device. Our solution is designed to solve the issue minimum interrupt to the usual routine. By protecting your precious talent assets, you are also contributing to epidemic prevention. The following examples will show you how you can also play a part in the international defencing league.
Application
Identification and Body Temperature Screening
Using state-of-art facial recognition and temperature screening technology at the entrance of the open space. When detected an unauthorized or abnormal temperature, access permission won't be given.
Body Temperature Got Recorded and Linked with Access Control

Records the body temperature of staff (registered user) is recorded with time and AIO location. Such information can be used as entry and exit records cooperate with the enterprise attendance SOP.
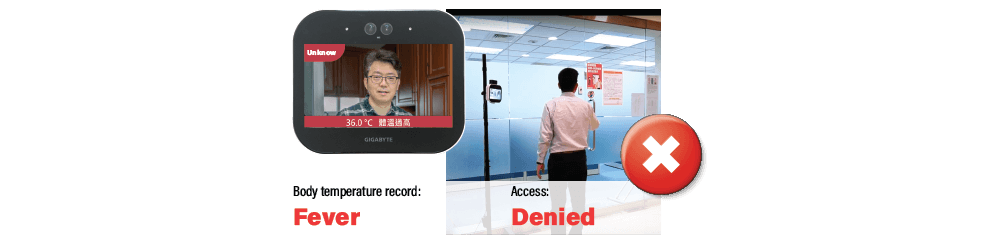
Based on our strong background of access control management, the protection not only contains registered users. Body temperature, time, and AIO location of any attempted access from an unregistered user will also be recorded.
Benefits
Reduce Manpower Workload
Integrate temperature detection and facial recognition with access control to enhance security and save the required manpower.
Security Level Upgrade
If strangers are found or an abnormal temperature is detected, the system will automatically record and administrator can continuously track.
Easy Integration of System
Flexible architecture is ideal for organizations of any size or development stage, we can adjust to your needs and integrate with your system.
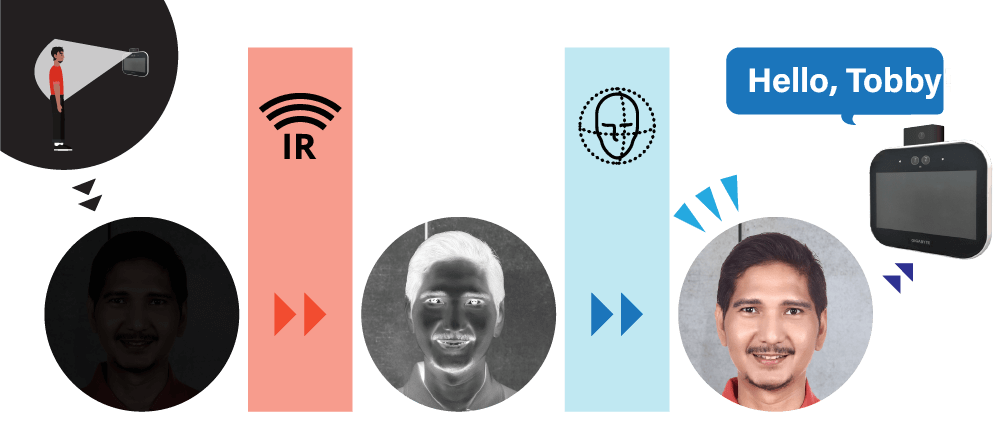
Scotopic Vision
Thanks to the duo lenses, the recognition works perfectly even in insufficient ambient light.
Product
This total solution including face recognition and access control system, back-end facial recognition server, and a front-end identification device: AIO-M2.